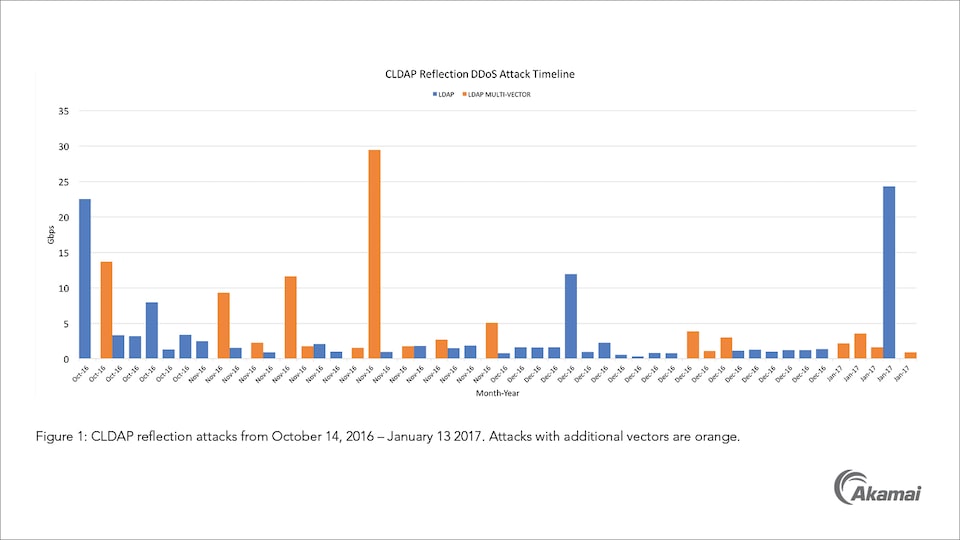
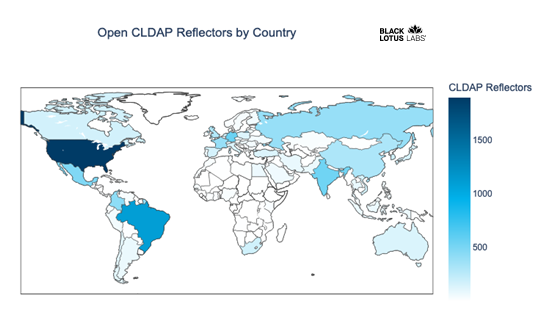
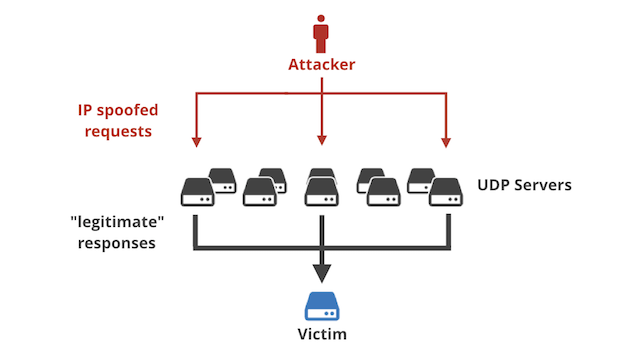
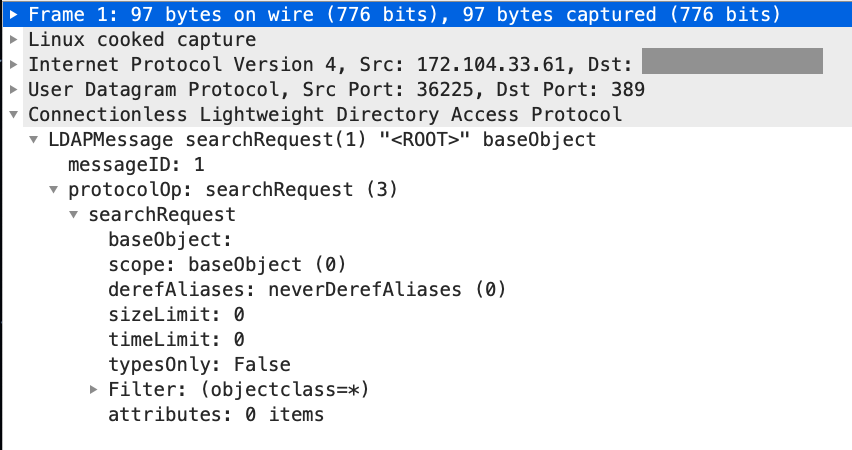
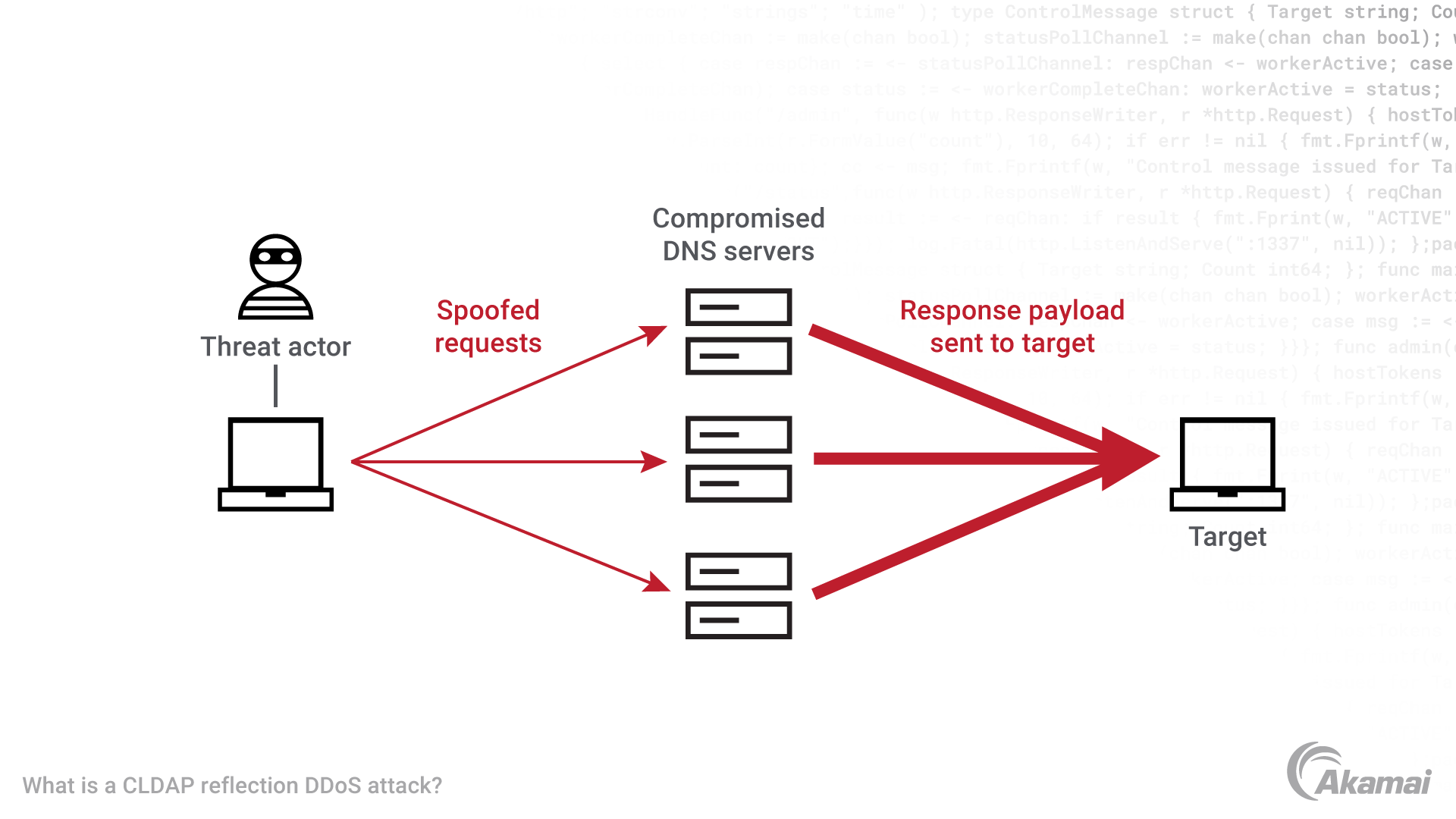
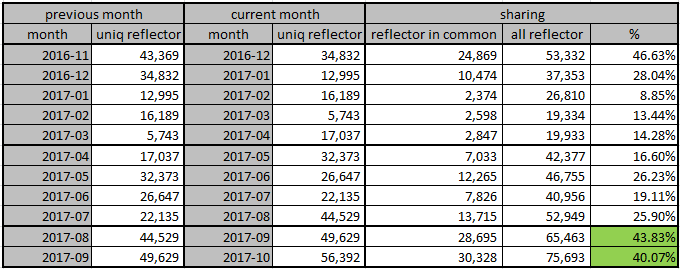
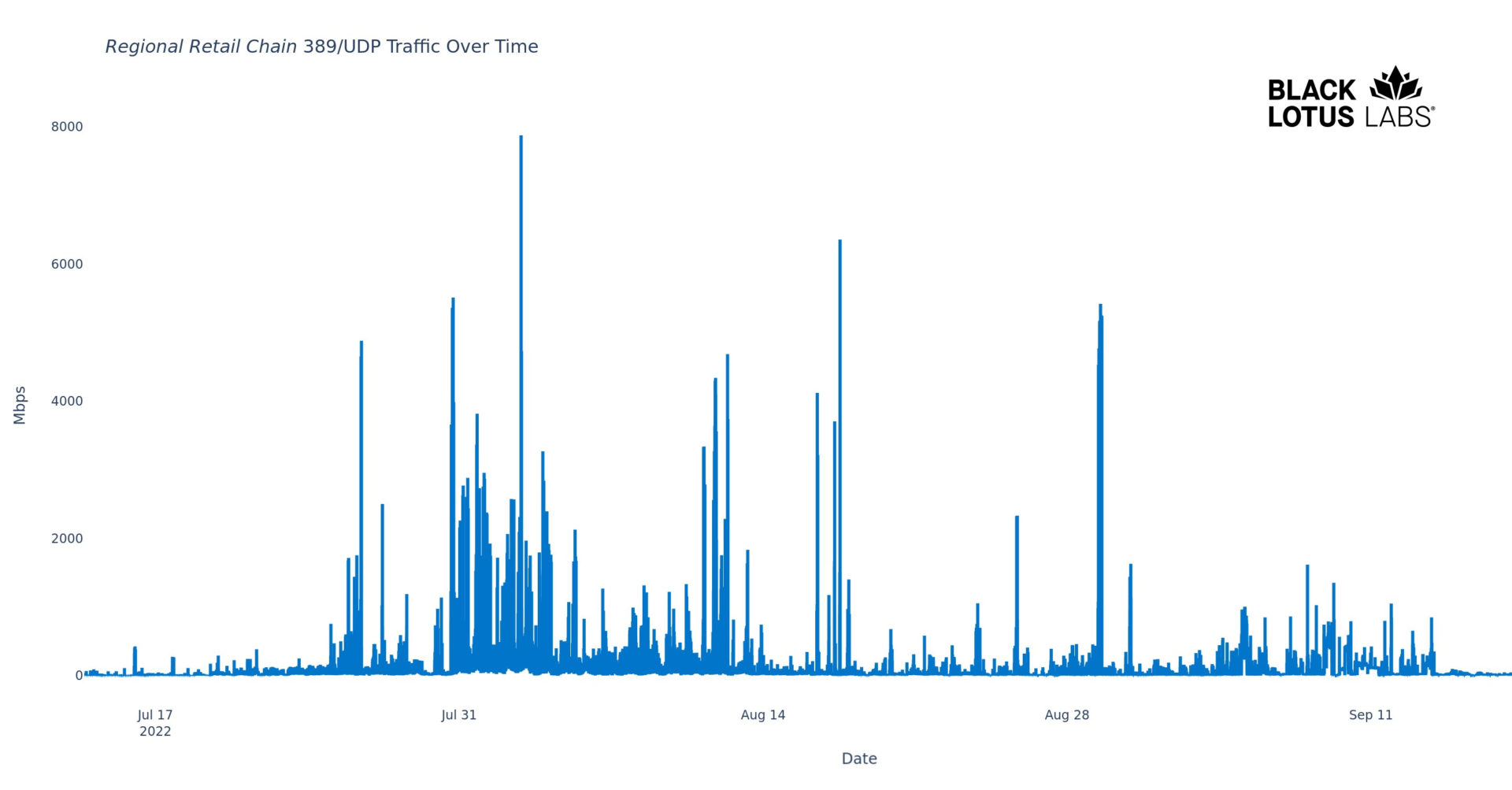
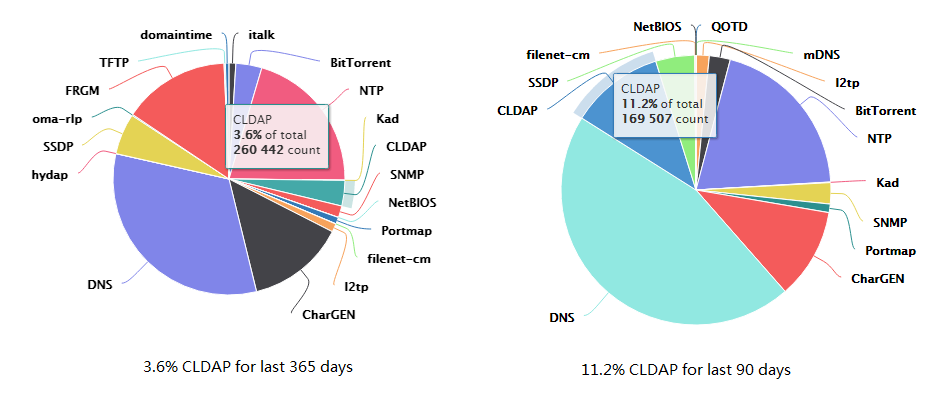
A study on reduction of DDoS amplification attacks in the UDP-based CLDAP protocol | Semantic Scholar

CLDAP Reflection Attacks back in style for the spring 2020 collection | DOSarrest Internet Security| DDoS Protection

Reflection Amplification Vectors: a Chronology - Link 11 - Take your cybersecurity to the next level